Hackers are turning inboxes into danger zones.
Google has issued an urgent warning to its 3 billion Gmail users after confirming a “sophisticated” phishing scam targeting unsuspecting emailers — and the cyber crooks are so sneaky, even seasoned techies are falling for it.
Developer Nick Johnson sounded the alarm on social media — after nearly getting duped by a con so slick it used Google’s own infrastructure to look legit.
“Recently I was targeted by an extremely sophisticated phishing attack,” Johnson posted on April 16.
“It exploits a vulnerability in Google’s infrastructure, and given their refusal to fix it, we’re likely to see it a lot more.”
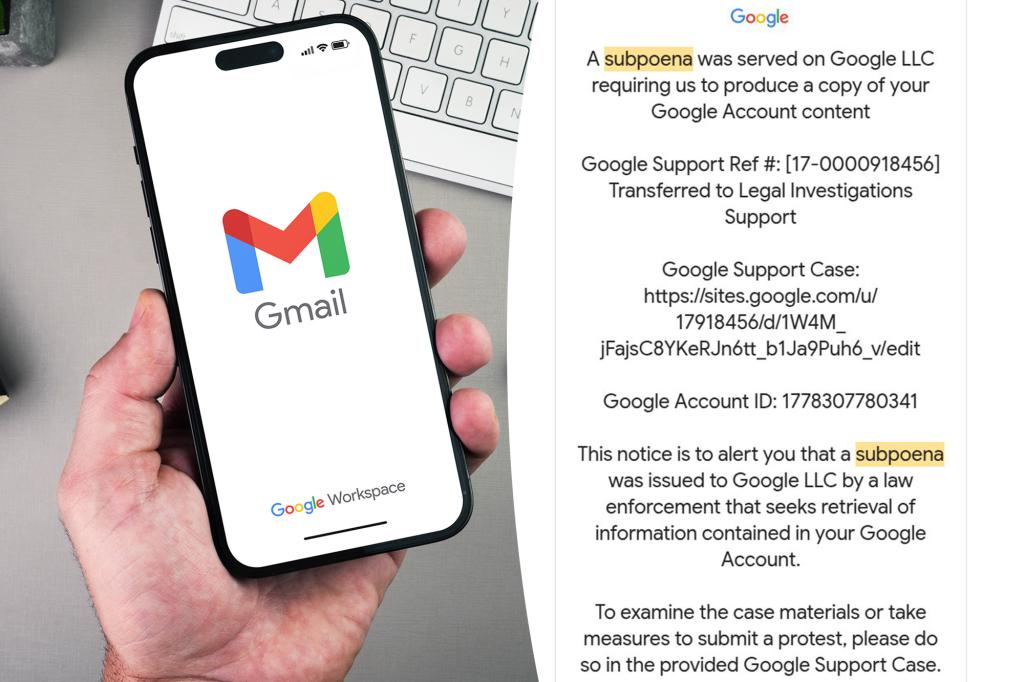
The trap came disguised as an official-looking email claiming he’d been hit with a subpoena tied to his Google account.
It even came from what appeared to be a real Google address.
“The only hint it’s a phish is that it’s hosted on sites.google.com instead of accounts.google.com,” Johnson noted in the X thread.
Clicking the link led to a bogus “support portal” with dead-on duplicates of real Google login pages — designed to trick users into handing over their credentials.
“From there, presumably, they harvest your login credentials and use them to compromise your account,” Johnson warned.
“It even puts it in the same conversation as other, legitimate security alerts.”
Worse yet, the shady email passed Google’s DKIM (DomainKeys Identified Mail) check, meaning Gmail treated it like just another ho-hum message.
In a recent statement to The Daily Mail, a Google spokesperson said, “We’re aware of this class of targeted attack from this threat actor and have rolled out protections to shut down this avenue for abuse. In the meantime, we encourage users to adopt two-factor authentication and passkeys, which provide strong protection against these kinds of phishing campaigns.”
Google says it’s already blocked the loophole that enabled the scam — and has rolled out fresh advice to help users dodge similar email traps.
“Google will not ask for any of your account credentials — including your password, one-time passwords, confirm push notifications, etc. — and Google will not call you,” the spokesperson emphasized.
Cyber creeps behind the scam used Google Sites to lend their ruse an air of credibility, banking on the fact that most people won’t second-guess a familiar-looking URL.
“These scams are designed to look as real as possible,” Johnson said, warning that many users won’t notice the slight tweak in the domain name — which could mean major headaches for their bank accounts or identity.
Gmail users relying solely on passwords are especially vulnerable.
If a hacker nabs your login info and you don’t use two-factor authentication (2FA) or passkeys, they can waltz right into your account.
A passkey, on the other hand, is a hardware-tied login method that hackers can’t just swipe and use — making it a much safer bet.
Meanwhile, phishing attempts are getting harder to spot. Red flags include vague greetings, an urgent tone, and clickable links demanding immediate action — especially regarding personal data or account access.
Even though Google does send emails about account issues, the tech titan says you should always think twice before clicking.
According to Google’s Privacy and Terms page, “When we receive a request from a government agency, we send an email to the user account before disclosing information. If the account is managed by an organization, we’ll give notice to the account administrator.”
And just in case you think you’ve got it figured out, Google adds: “We won’t give notice when legally prohibited under the terms of the request. We’ll provide notice after a legal prohibition is lifted, such as when a statutory or court-ordered gag period has expired.”
Bottom line: If you get a sketchy-sounding email asking for personal info, don’t click.
Instead, open the site in a separate browser window and double-check the source.